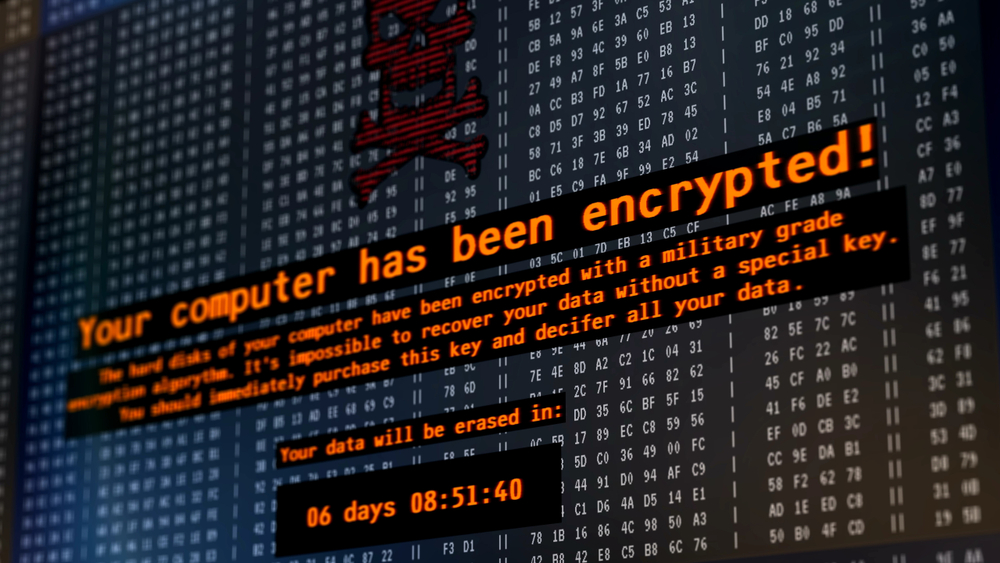
How ransomware cyber attacks work
In most cases, these cyber attacks are carried out by:
– Downloading ransomware disguised as an e-mail attachment, by downloading software or attachments from applications, suspicious/infected sites;
– Exploiting a gap in the security of computer devices or systems.
Types of ransomware and how to identify them
The term “ransomware” covers a lot of different types of malware. What they have in common is the threat of deleting or retaining data in an attempt to force a ransom.
There are the four types of ransomware that are most used by hackers, which we will discuss further.
Post Views: 351